SQLMap | Kali Linux Tools Cheatsheet
SQLMap Cheatsheet The Ultimate SQL Injection Tool Reference Guide 🔍 Basic Usage Target Specification Request…

SQLMap Cheatsheet The Ultimate SQL Injection Tool Reference Guide 🔍 Basic Usage Target Specification Request…
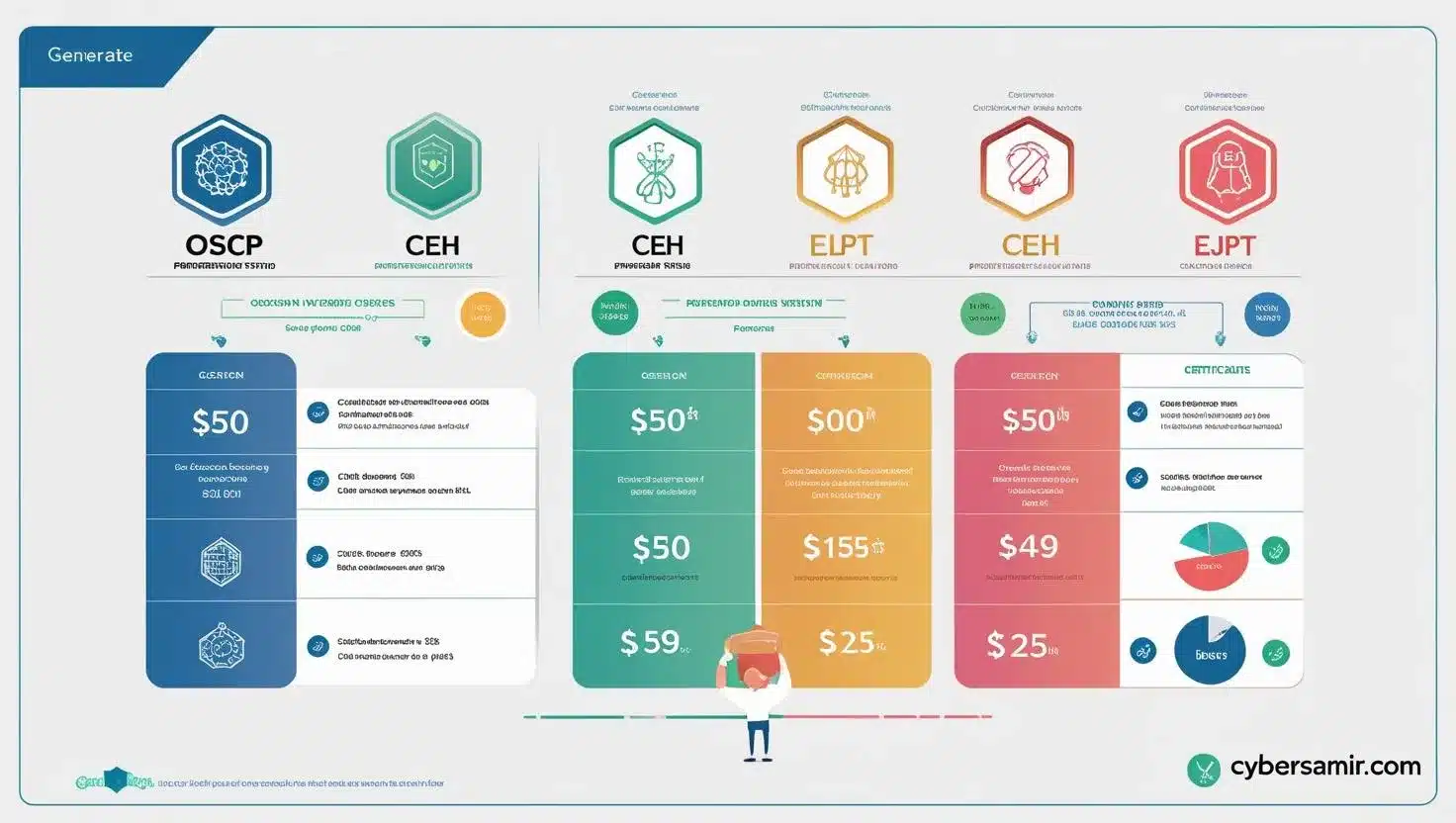
Penetration Testing Certifications: OSCP, CEH, eJPT Compared Penetration Testing Certifications: OSCP, CEH, eJPT Compared An…

Remote Code Execution (RCE) Vulnerabilities Explained Remote Code Execution (RCE) Vulnerabilities Explained The complete guide…
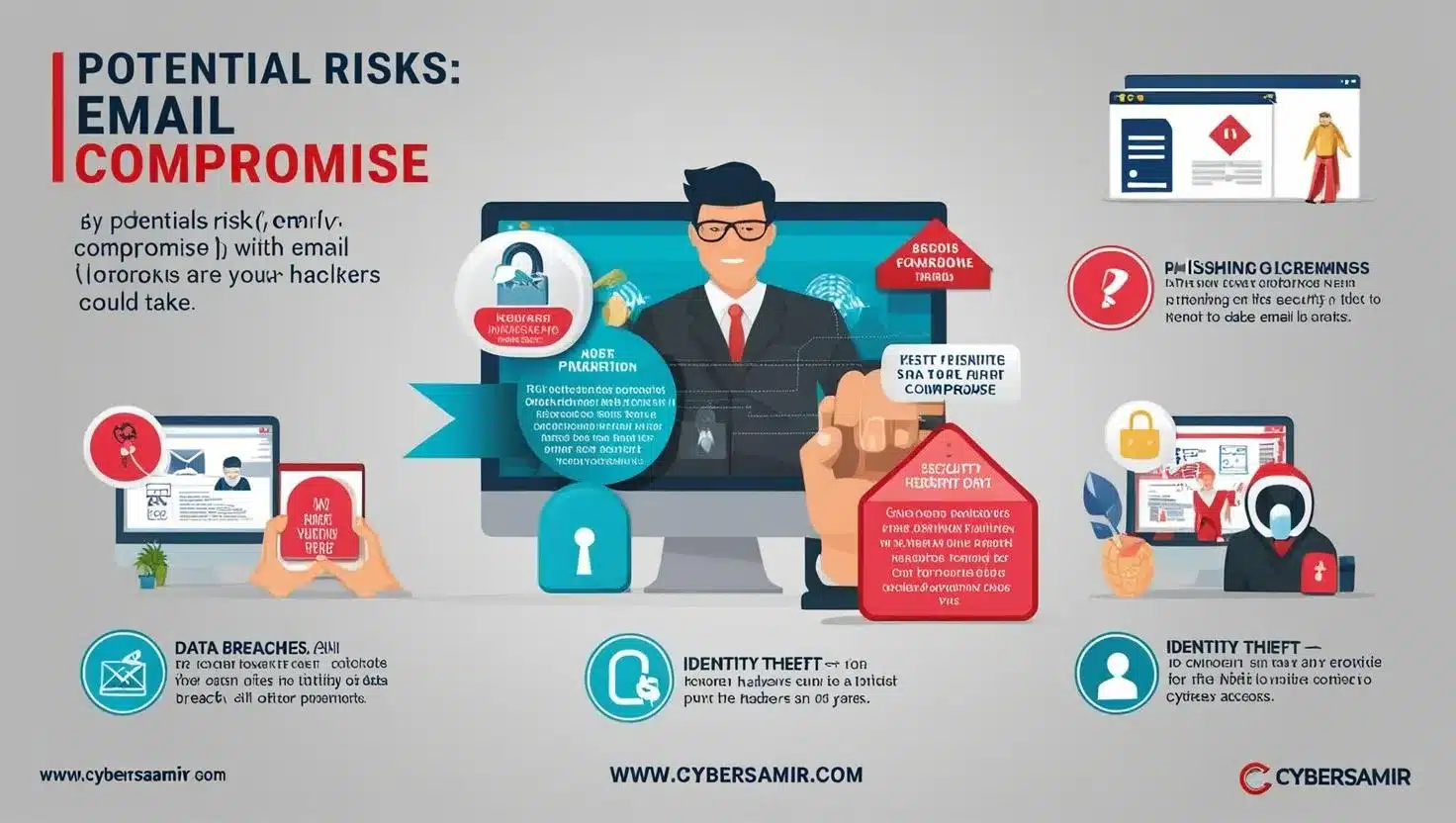
Welcome to Cybersamir’s Cybersecurity Corner! In this blog, we’ll explore a question that might keep…
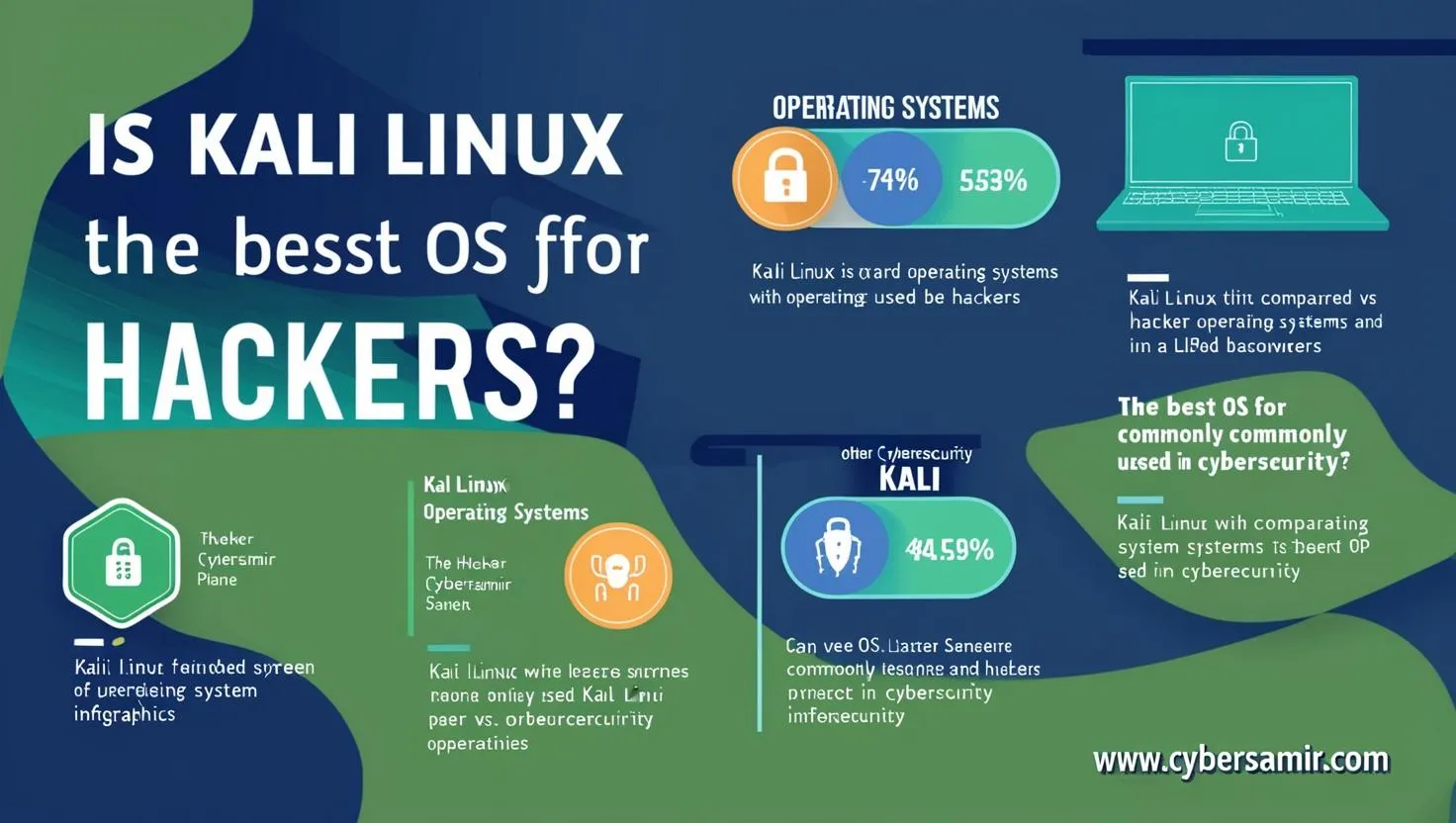
1. Introduction Kali Linux is widely recognized in the hacking community as a powerful tool…
Linux commands are the backbone of interaction with the Linux operating system, allowing users to…

Penetration testing, often referred to as ethical hacking, plays a critical role in cybersecurity by…